You can protect yourself from malicious cyber threats by understanding the types
What is Phishing?
Phishing is the activity of defrauding an online account holder by posing as a legitimate company or user. The Phishing attempt becomes successful when the content of the email, file or link are opened or clicked.
Software that are used for phishing are also referred to as Malware, Trojan or Virus. Methods of phishing range from malicious websites to spamming.
How will I know that I have been phished?
You may never know. In severe cases, it could take months before you realize that your account has been compromised.
How can you prevent phishing?
Simply put, do not:
click on unfamiliar links
visit unfamiliar web sites
open unfamiliar files
open unfamiliar forms
respond to suspicious emails
Always verify the sender’s email ID, not the name, if the email looks suspicious or if the request is related to sensitive information.
How is phishing manifested?
Successful phishing may occur when you:
- click on a link and disclose your credentials – we name this a deceptive phishing attempt
- click on a link (just that!) – a website can be fraudulent (while it may offer something great) and thus becomes a trap to acquire your information – we refer to this as Search Engine Phishing
- open a foreign file – we refer to this as Malware-based phishing
- browsing a malicious site – where malicious software will track your keystrokes thereon – we refer to this as key or screen loggers
- receive a pop-up message to change your computer configuration (e.g. allow pop-ups) – we refer to this as System Reconfiguration
- someone pretending to be a co-worker or supervisor in order to make a financial transaction or other
- receive a phone call from someone suggesting to access a website for a prize, or claim that they are from a company (not legit) – we refer to this as Phone Phishing
It’s phishing season…don’t get caught!
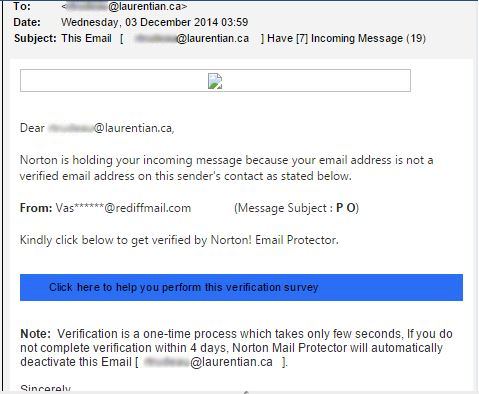
Hints on how to detect a fraudulent email
At first glance, the email looks like it is coming from a legit user. Upon closer look, the email becomes suspicious…
- “you have refuse…”
Hint: Grammatical errors (should be “refused”) are a sign of spam and phishing attempts. - “… update your mailbox …”
Hint: Account updates are done via HR or Registrar only. - The link (the domain http://forms3.createonlineforms.com) is not a Laurentian domain.
Hint 1: Laurentian domains start with https:// (s=secure).
Hint 2: Laurentian has the following domains <domain>: laurentian.ca, laurentienne.ca, lul.ca. A suffix in front of the domain like www3 or sspr is ok as long as the last characters of the domain (before the first “/”) is <domain>.ca.
Examples of good and bad domains
sspr.laurentian.ca = Good
laurentian.sspr.ca = Bad
Through phishing, your data can be unintentionally encrypted by Ransomware
and can only be retrieved if you pay a ransom!
What is Ransomware?
Ransomware is a type of malicious software designed to block access, typically through encryption, to data files or a computer system until a sum of money is paid.
Ransomware is horrible because if you do not have a backup, you will not be able to access your data until you paid a ransom, and if the hackers provide you with the key to un-encrypt!
Ransomware can identify all data on your computer and on networked storage.
IT can only help you restore your files if there is a backup of the files prior to the encryption.
How can I fix Ransomware?
You only have 2 options:
- Laurentian Approved: Delete infected files and replace with your backup files
- Not Approved by Laurentian: Pay Ransomware (note that LU will not reimburse Ransomware payment).
Lost or Stolen Data
In the event that your computer, mobile device or your data is lost or stolen, you must immediately communicate with LU IT at x.2200 or the CIO at x.2277.
At that time, you will be asked the following questions:
- To catalogue the missing data such as type of data, type of confidential fields within the data, the range of the missing data (1st year students, account numbers starting and ending with …).
- Who could have the missing data and how they could use the data
- The time and the location of the incident
- To produce a copy of the missing information (from backup or other) if possible
- To reset your Laurentian password
Simple step = immense impact
Keylogger
Hardware devices called keyloggers can capture computer keystrokes such as login information and passwords by tracking the keystrokes used at a workstation.
To prevent this, you need to visually inspect your desktop computer to determine if a keylogger device is attached. Physical keyloggers cannot be detected by software. While it can be any shape or colour, a keylogger will look like an innocuous connector between the computer’s keyboard cable and the USB port.
If you find a hardware keylogger installed on a university desktop computer, please contact IT immediately.
Foreign USB Stick
You must not connect a foreign USB stick or foreign removable device into your LU computer, even if it is shared by an unknown person. 45% of foreign USBs have known to be a source of attack.